Corporate networks are so complex to administer that holes in the system are inevitable. The temptation to multiply cyber solutions to fill security gaps is great. With the support of the Thales Digital Factory, the group’s incubation programme, the Chimere spin-off proposes a new way of conceiving networks and thinking about perimeter security.
Widely deployed today, the principle of perimeter security consists of dividing internal networks into distinct zones and configuring firewalls so that they only allow flows considered valid by the network security policy. But in many cases, attackers are able to bypass these blocks by spoofing authorised IP addresses or performing man-in-the-middle attacks. Created in November 2022, the Chimere spin-off is based on a totally Zero-Trust approach to network access. Interview with Guillaume-Alexandre Chaizy-Gostovitch and Gabriel Ladet.
Can you introduce yourself and your startup? What is your connection with the Thales group and the Thales Digital Factory?
We are two cybersecurity engineers from the Thales group. We worked for the company for five years during which we assisted clients of all sizes and sectors with their security issues. Guillaume-Alexandre worked on Thales’ Blockchain offering, while I worked on offensive security and penetration testing issues.
During our missions, we supported many clients who were victims of compromise. Our post-mortem analyses revealed recurring attack vectors despite the application of best security practices.
In many cases, they were not to blame. When an attacker enters a network by exploiting a zero-day vulnerability on a VPN gateway exposed on the internet, it is difficult to justify a fault in the application of a process or patch management. Enterprise networks are so complex to administer that holes in the net are inevitable. This is without mentioning the fact that they rely on protocols as old as the Internet and rely on successive cyber solutions to fill their security gaps. We thus wondered if there was something to change in the way we approached security today.
Are the solutions we use really adapted to current threats?
In parallel with our missions, we experimented with a number of ways to approach the subject. We tried to abstract from the current practices and recommendations in terms of network architecture or secure remote access. This intellectual exercise is never easy: breaking out of the framework in which we are used to evolving is a bit like learning to walk again. However, after several weeks of research and a first proof of concept, we realized that we might have something interesting. We presented the idea in an internal Thales competition, which allowed us to obtain initial funding. After an additional R&D phase, we were recommended to apply for the Thales Digital Factory Start-Up Studio: the group’s incubation program.
This is when Chimere was truly born. This high-quality support allowed us to achieve what we could not have done alone. This overhaul of our technical knowledge was now followed by a total reset of all the aspects with which we, technical engineers, were not familiar: business, marketing, value proposition, pitch, or finances. For three intense months, we were brought to test our value proposition on the market and realized that the idea we had initially identified could perhaps fit into a broader and more impactful vision. We pivoted our approach, obtained early large account partners to follow us in the adventure and then pitched to the senior Thales management for the funding that later allowed us to recruit the six members of the team, develop the solution and obtain the MVP that we currently have.
In order to go faster, Chimere became a legal entity in its own right in November 2022. Of course, we continue to be supported by Thales and the Thales Digital Factory, who closely follow our progress and are always good advisors. The fact that the project was born at Thales marks our way of thinking and the way we approach security issues in a lasting way. We take advantage of this experience and the reflexes acquired within the group are reflected in our way of thinking and acting on a daily basis.
Can you present the Chimere project and the underlying technology? What are the innovative or disruptive aspects in terms of security?
Chimere is an innovative way of designing network security, the concept of perimeter, trust, and exposure of services on the Internet. When the Internet came into existence in the 1980s, it was a trusted network in which all users could expect to communicate without fears. TCP/IP was even designed on this premise: even today, anyone can publish a service on the network and make it accessible to all users through an IP address and a port. Knowledge of these two pieces of information is sufficient to establish a connection with the associated service.
As the Internet expanded and became global, cyber-threats appeared in response to this model that was not designed to cope with them. Attackers continuously scan the network, discover vulnerable services, and then compromise them using identifiers they have recovered from a data leak, phishing, or exploiting a vulnerability.
This principle is far from new, just go back to 1988 with the Morris worm to realize that it is part of the very foundation of the Internet. This threat, which received good media coverage at the time, exploited vulnerabilities in sendmail and fingerd services exposed on the Internet. Automatically, the worm scanned the network, detected services, then infected them before continuing its progression. Almost 30 years later, in 2017, the Wannacry worm used the same process by exploiting a vulnerability affecting SMB services exposed on the Internet, and replicating itself automatically. In four days, over 300,000 machines were infected, and the ransomware became globally known.
This issue is not restricted to the Internet. Private networks, based on the same communication protocols, are even more affected. On the one hand, organizations consider that the trust that can be given to a user within the network is higher than the trust that can be given to a user outside. On the other hand, some attacks (MITM, IP Spoofing, TCP session hijacking) are much easier to carry out within a private network than from the Internet, giving internal attackers additional weapons. Thus, it is common to divide internal networks into distinct zones, depending on the trust accorded to them, using firewalls that will only allow flows considered valid by the network’s security policy. This perimeter security principle is widely used today.
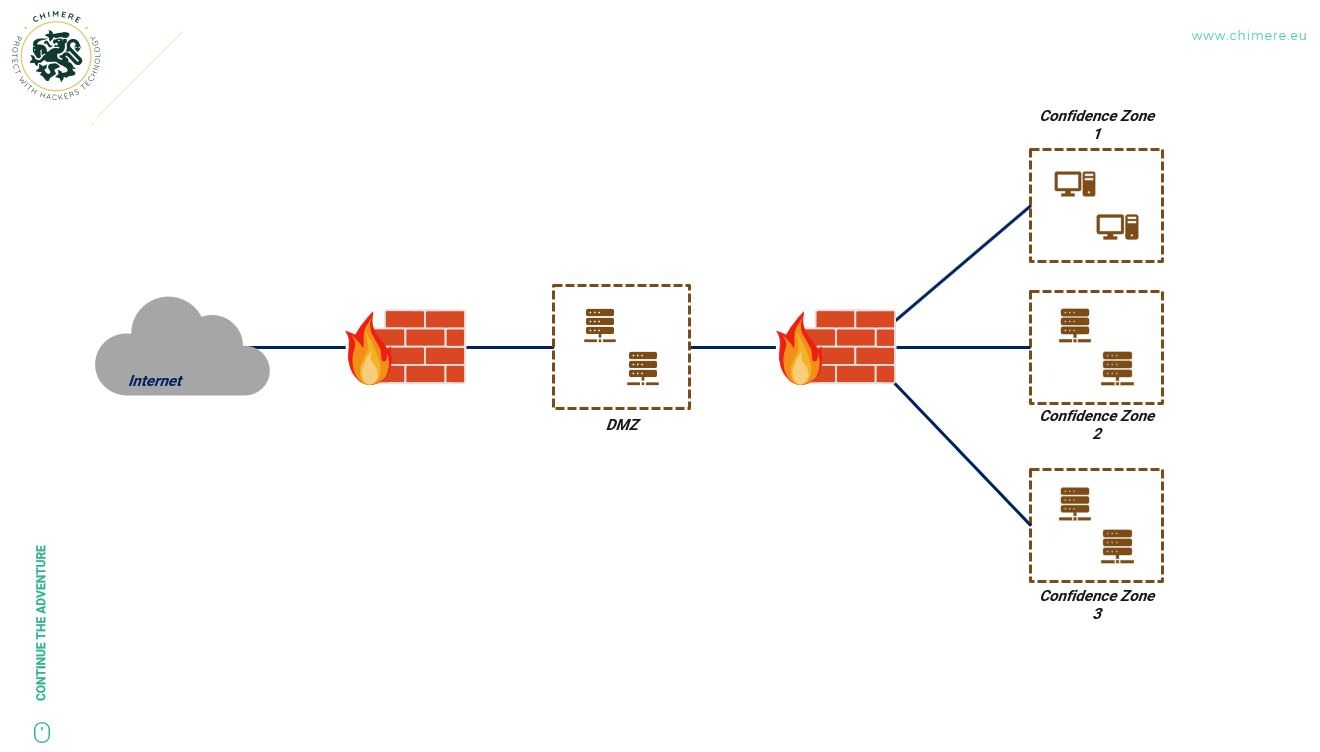
Often, firewalls are used to finely segment access to services and ensure that only certain positions or machines can access specific services. Filtering rules are based on the historical quartet of TCP/IP: the source IP address, the source port, the destination IP address, and the destination port.
In many cases, attackers are actually able to bypass these blockages by impersonating authorized IP addresses or by performing man-in-the-middle attacks. Within the same trust zone, it is often easy for them to perform lateral movements and take possession of additional machines to facilitate hops elsewhere in the network. Of course, adding more and more security mechanisms and solutions only feeds the principle of defense in depth. In no way do we renounce this fundamental principle. We are simply considering a new way of designing networks and thinking about perimeter security. When we started thinking about Chimere, it seemed obvious to focus on one of the first mechanisms offered by TCP/IP: the principle of exposing services. With TCP/IP, the service is listening on a network interface and is requested by a client who requests the establishment of a connection. The service is considered to be in a « passive » state, which means it accepts connections from clients as long as they know the associated IP address and port.
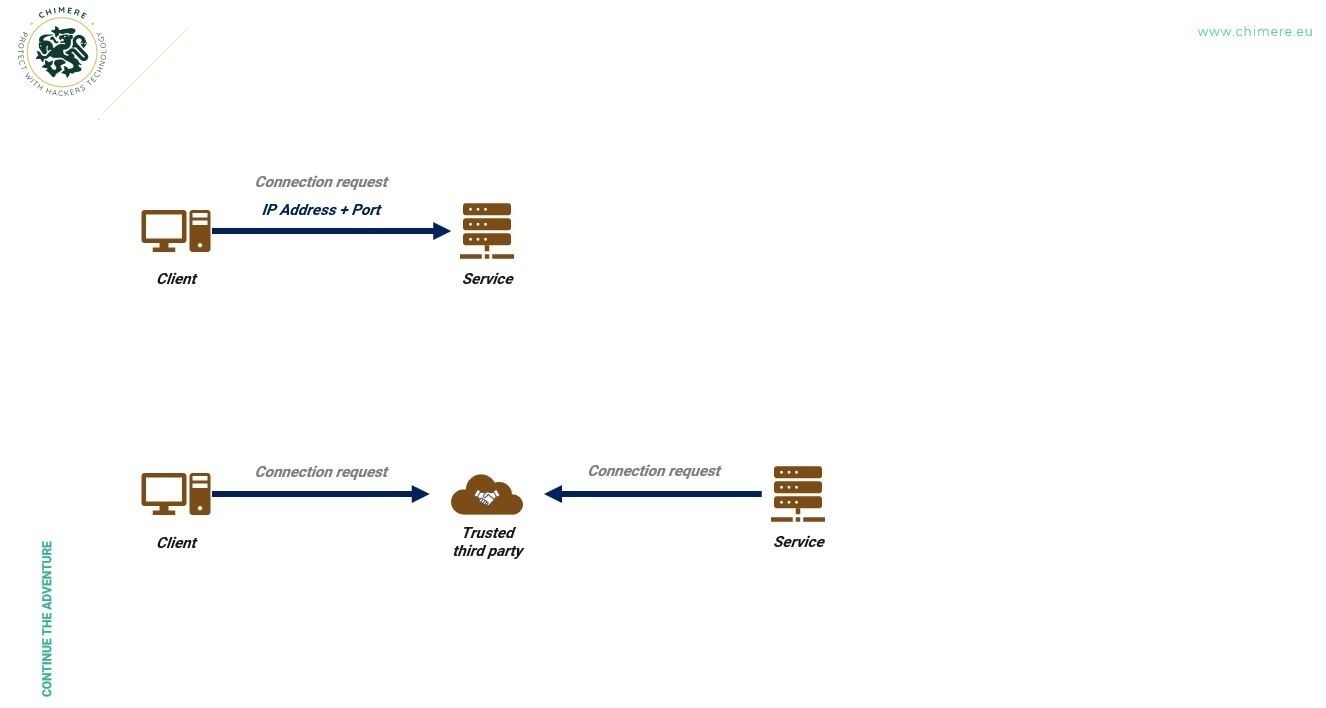
The first paradigm shift consisted of changing this mechanism. To avoid wild network scans, it is necessary to prevent the service from listening and accepting connections requested by clients by default. Obviously, and still based on TCP/IP, there is a naive way to solve this problem: it is sufficient to introduce a trusted third party actor on the network that will serve to interconnect users and the service: On the one hand, clients connect to the trusted third party just like they could with the service before. On the other hand, the service connects to the trusted third party, who serves as an intermediary between clients and the service. Additionally, an encryption layer is added between each player to avoid typical privacy problems.
When considering the client and the final service, the TCP flows become exclusively outgoing (at least at the connection establishment stage, of course, messages flow in both directions). This way, the service can avoid being in listening mode on a network interface accessible by malicious actors and is no longer detectable by attackers’ wild scans. However, this model introduces a new problem: one must trust the intermediary. If the latter is compromised, the attacker can establish a connection with the service. They can also cause a denial of service by making the intermediary unavailable. And if there is no end-to-end encryption, they can spy on the conversations. All without, of course, forgetting that the intermediary itself is an exposed service, as it must accept connections from clients and also from services.
In the end, is this model not just a way to move the problem?
It is if the intermediary does not have some essential properties.
Imagine that this new system has the following characteristics:
- It must be possible not to have to trust the intermediary on the « confidentiality of messages » aspect that passes through it. It must not be able to read the messages between clients and the service. This aspect is the simplest to achieve: just integrate an end-to-end encryption mechanism.
- It must be possible not to have to trust the intermediary for the « access to the service » aspect. This means that it must not be able to establish a connection with the service that is made available through it. Only authorized clients should be able to (for example, using a cryptographic element).
- It must be possible not to have to trust the intermediary for availability. This can, for example, be spread out between several actors and organizations. Given the two previous characteristics, this functionality is feasible since no actor will be able to read the content of messages or access the services without the appropriate cryptographic element.
These characteristics even allow the intermediary to be exposed on the internet without compromising the security of the services made accessible.
If these three conditions are met, then the model makes perfect sense: it fits into a completely Zero-Trust network access approach. There is, in fact, a term for such a model, invented by Gartner in 2019: ZTNA (Zero-Trust Network Access).